Kubernetes for ML: A Developer’s Practical Guide
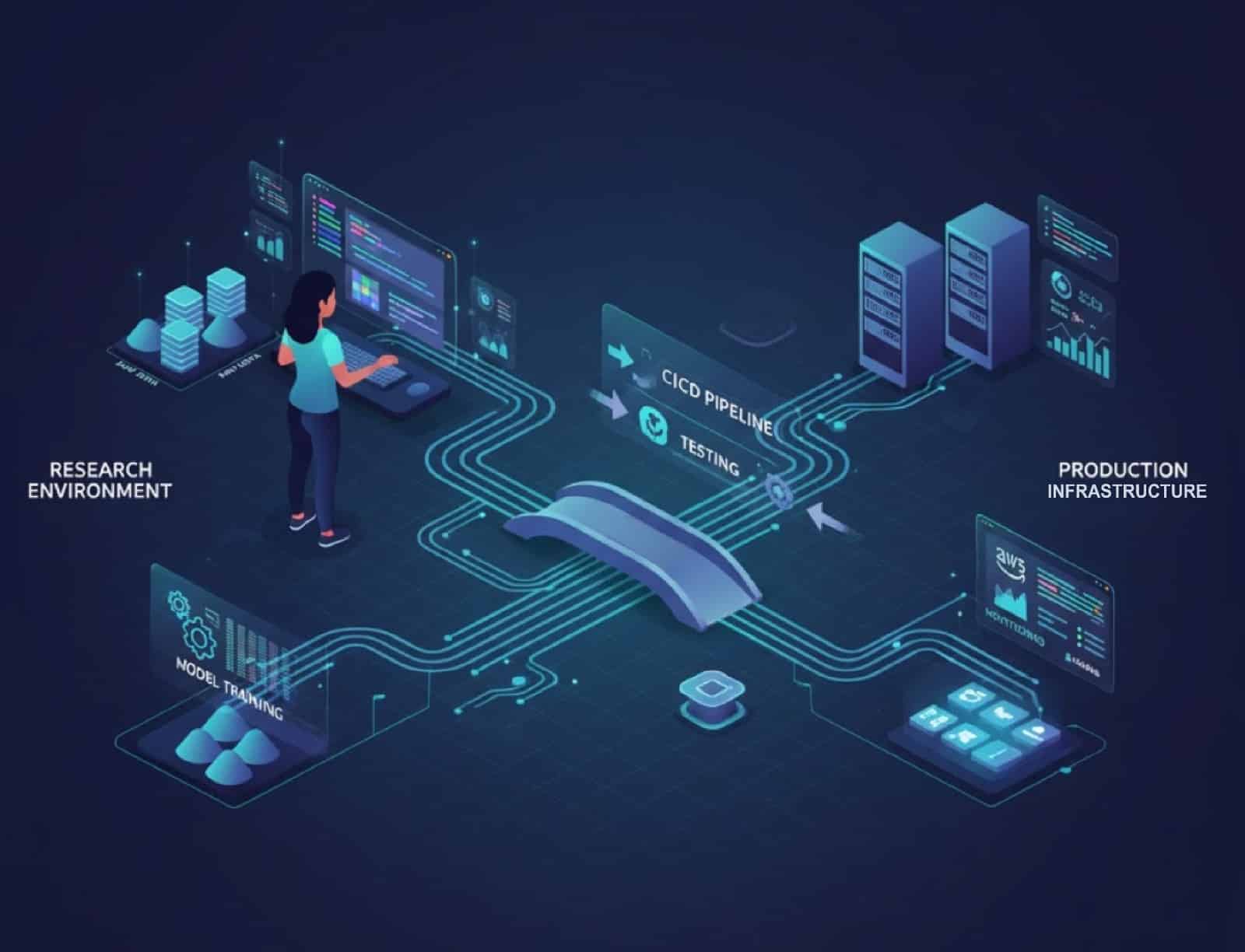
Modern ML engineers and platform developers know that scaling machine learning workloads isn’t a matter of just adding GPUs. Optimizing ML system performance requires orchestrating compute, storage, and data pipelines to maximal efficiency under production constraints. As models grow more complex, what once was processed within a single rack now requires distributed GPU clusters, shared … Read more