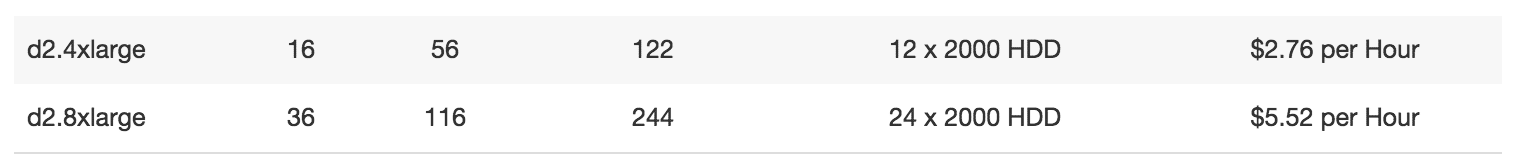
Introducing the Cloud-Monolithic Computing Foundation
Raise your hands if you started the virtualization journey using oversized virtual machines <raises hand>. Let’s face it, we are in the process of making the same mistakes in the cloud that we did with early virtualization. It’s ok. As many of the world’s leading open source and closed source traditional vendors lean forward to … Read more