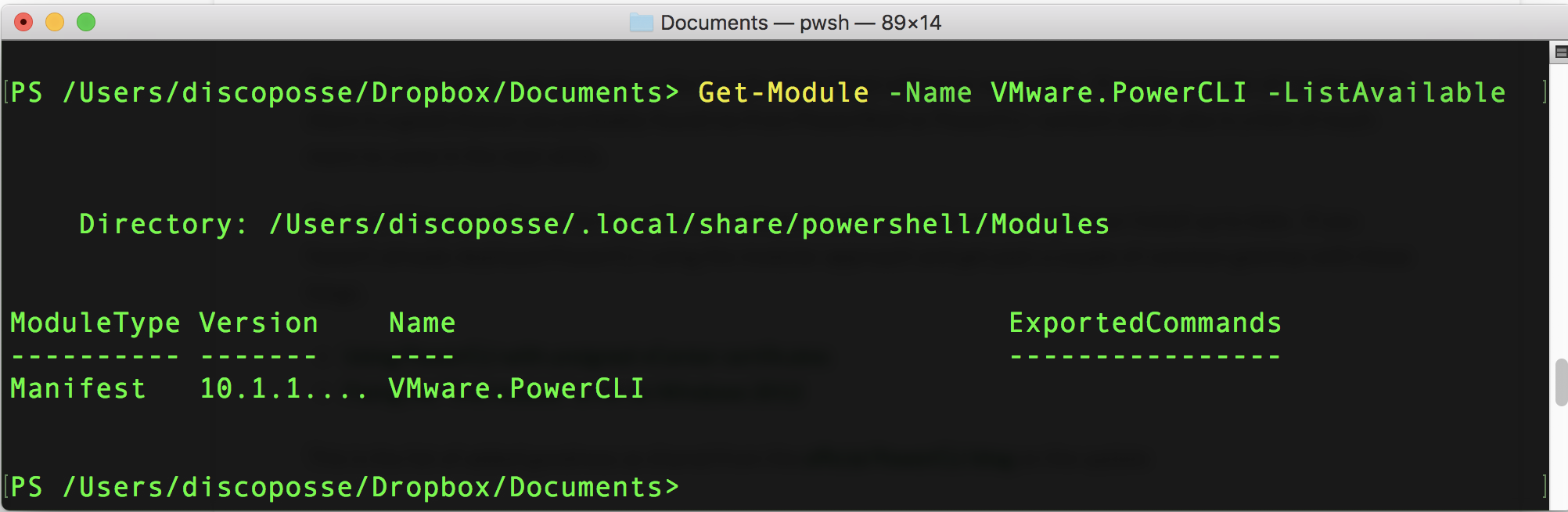
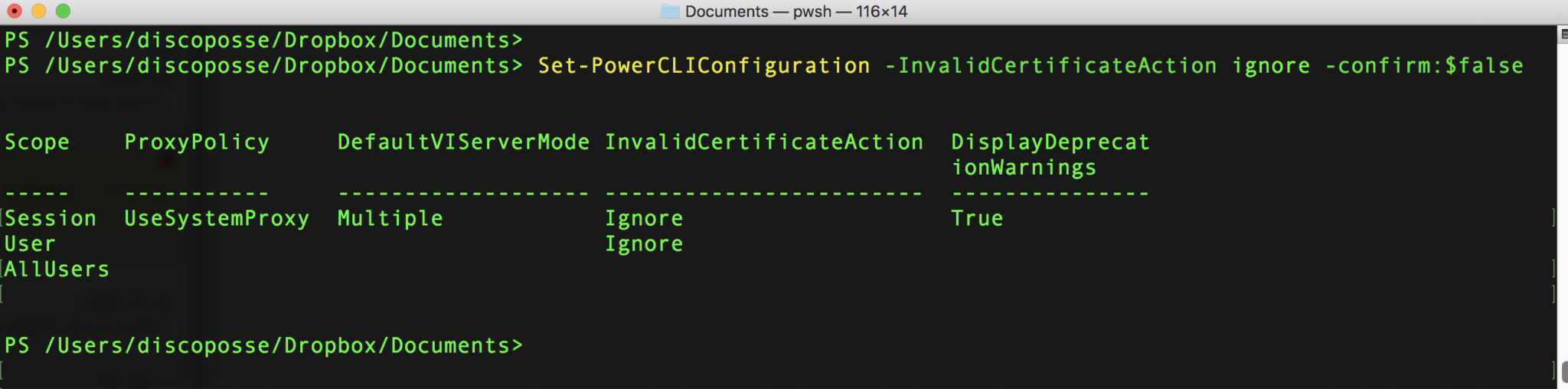
PowerCLI 11.0 is Out – Easy Update and Features Galore!
PowerCLI fans unite and celebrate as the launch of the latest edition is now public. If you’re a reader of my blog then there is a good chance you probably found me from PowerShell or PowerCLI content which also is a hint of much more to come in the next while. The first thing you … Read more